In today’s digital landscape, managing IT risks is paramount for business success. At Pro Hockey Advisors, we understand the critical role of a robust Information Technology Risk Management Framework in safeguarding operations and data.
This guide will walk you through the essential steps to create an effective framework, tailored to your organization’s needs. We’ll cover risk identification, mitigation strategies, and best practices to help you stay ahead of potential threats.
What is IT Risk Management?
Definition and Scope
IT Risk Management is the process of identifying, assessing, and controlling threats to an organization’s digital assets and infrastructure. This practice protects sensitive data, maintains operational integrity, and safeguards against potential cyber threats.
The Growing Importance of IT Risk Management
In today’s hyper-connected business landscape, the stakes for IT security have reached unprecedented heights. A report by Cybersecurity Ventures projects cybercrime costs to reach $10.5 trillion annually by 2025, a substantial leap from the $3 trillion recorded in 2015. This staggering figure underscores the urgent need for organizations to prioritize IT risk management.

Sports organizations face particularly acute risks. Player contracts, medical records, and strategic plans are prime targets for cybercriminals. A single data breach could result in millions of dollars in losses and irreparable damage to an organization’s reputation.
Key Elements of an Effective IT Risk Management Framework
To build a robust IT risk management framework, organizations should focus on several critical components:
1. Comprehensive Risk Assessment
Organizations should start with a thorough inventory of their IT assets and identify potential vulnerabilities. This includes hardware, software, data, and human factors. Tools like vulnerability scanners and penetration testing can uncover weaknesses in systems.
2. Clear Risk Mitigation Strategies
After identifying risks, organizations need to develop specific strategies to address them. This might involve implementing new security technologies, updating policies, or providing additional staff training. Risks should be prioritized based on their potential impact and likelihood of occurrence.
3. Continuous Monitoring and Adaptation
IT risks evolve rapidly, so management frameworks must remain dynamic. Organizations should implement real-time monitoring tools to detect and respond to threats quickly. Regular reviews and updates to risk management strategies will address new and emerging threats effectively.
The implementation of these key components can significantly reduce an organization’s exposure to IT risks. A proactive approach to IT risk management not only protects assets but also enhances stakeholder trust.
As we move forward, we’ll explore the specific steps involved in creating a comprehensive IT Risk Management Framework. This process will help organizations build a strong defense against potential cyber threats and ensure the security of their digital assets.
Building Your IT Risk Management Framework
Identify and Assess IT Risks
The first step in building your framework is to conduct a thorough risk assessment. This involves creating a catalog of all IT assets, including hardware, software, data, and network infrastructure. A study by Ponemon Institute found that 60% of data breaches in 2022 resulted from unpatched vulnerabilities, which underscores the importance of a comprehensive asset inventory.
Next, evaluate potential threats and vulnerabilities associated with each asset. You can accomplish this through various methods such as vulnerability scans, penetration testing, and threat modeling. The OWASP Top 10 is a regularly-updated report outlining security concerns for web application security, focusing on the 10 most critical risks.
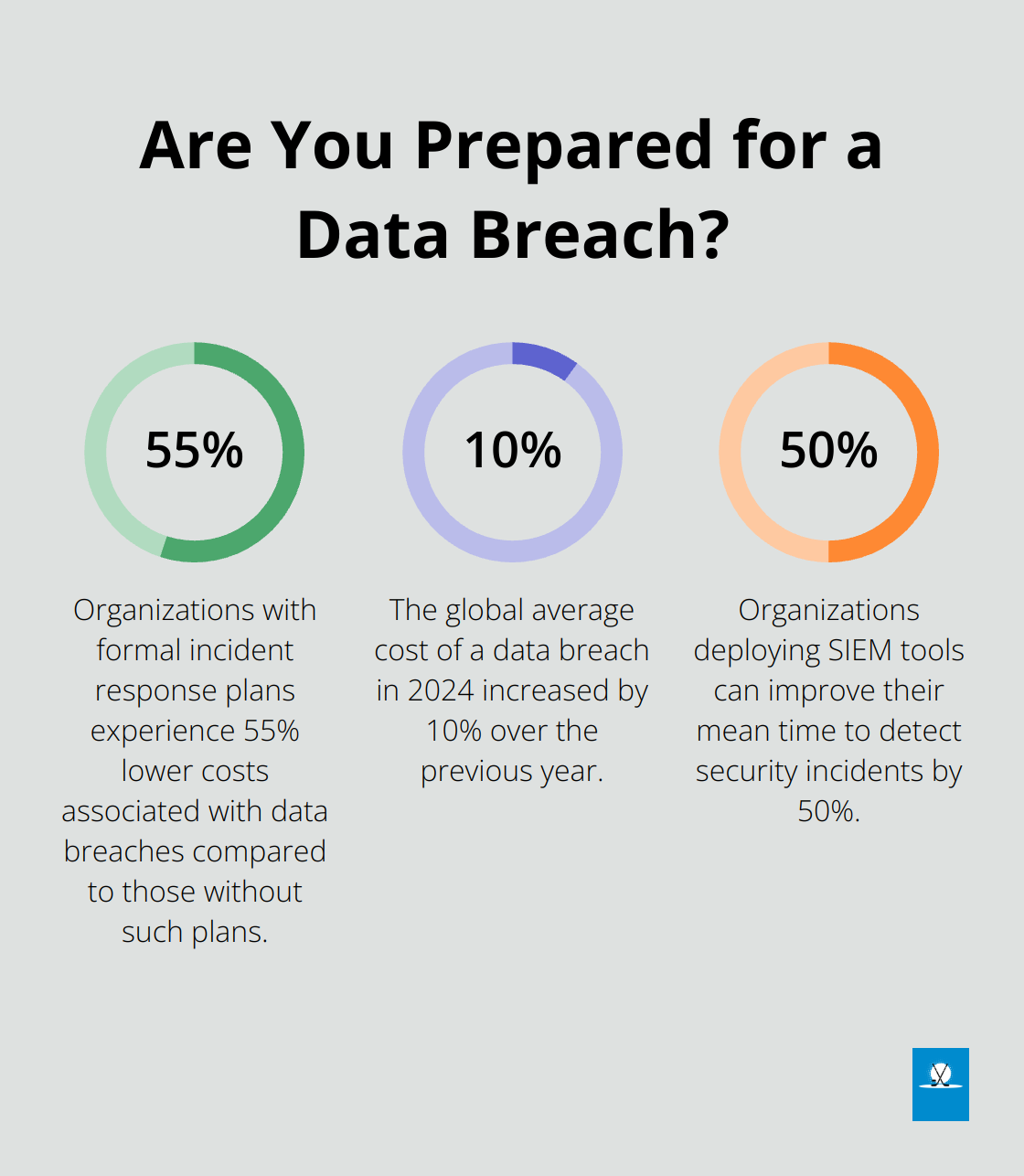
Quantify the potential impact of each risk. This involves estimating both the financial and operational consequences of a security breach. According to IBM’s Cost of a Data Breach Report, the global average cost of a data breach in 2024 reached $4.88 million, a 10% increase over the previous year and the highest total ever.
Develop Effective Mitigation Strategies
Once you identify and assess risks, the next step is to develop strategies to mitigate them. This involves prioritizing risks based on their potential impact and likelihood of occurrence. The NIST Cybersecurity Framework provides a useful structure for organizing mitigation efforts across five core functions: Identify, Protect, Detect, Respond, and Recover.
For each high-priority risk, develop specific mitigation tactics. This might include implementing new security technologies, updating policies and procedures, or providing additional staff training. For example, implementing multi-factor authentication can reduce the risk of unauthorized access by up to 99% (according to Microsoft).
Implement Controls and Monitoring Systems
With mitigation strategies in place, the next step is to implement controls and monitoring systems. This involves deploying security tools and technologies to enforce policies and detect potential threats. Some essential controls include:
- Firewalls and intrusion detection systems
- Endpoint protection software
- Data encryption tools
- Access control systems
Implement continuous monitoring to detect and respond to security events in real-time. Organizations that deploy security information and event management (SIEM) tools can improve their mean time to detect (MTTD) security incidents by 50% (as reported by Gartner).
Establish Incident Response Plans
Despite best efforts, security incidents can still occur. Therefore, it’s important to have a well-defined incident response plan in place. This plan should outline the steps to take in the event of a security breach, including:
- Containment procedures to limit the spread of the incident
- Eradication steps to remove the threat
- Recovery processes to restore normal operations
- Post-incident analysis to learn from the event and improve future responses
The SANS Institute reports that organizations with formal incident response plans experience 55% lower costs associated with data breaches compared to those without such plans.
Creating an IT risk management framework is an ongoing process that requires regular evaluation and adjustment to remain effective against evolving threats. As we move forward, we’ll explore best practices for maintaining and improving your IT risk management framework to ensure long-term success in protecting your organization’s digital assets.
Maximizing IT Risk Management Effectiveness
Align Risk Management with Business Goals
IT risk management must operate in tandem with overall business objectives. A Gartner survey found that 78% of CIOs believe aligning IT initiatives with business goals is essential for success. This alignment ensures that risk management efforts support rather than hinder business growth.

To achieve this alignment, organizations should:
- Involve business leaders in risk assessment processes
- Prioritize risks based on their potential impact on business objectives
- Develop risk mitigation strategies that balance security needs with operational efficiency
A professional hockey team might prioritize protecting player health data over securing marketing materials, as player health directly impacts team performance and success.
Cultivate a Risk-Aware Culture
Creating a culture of risk awareness is vital for effective IT risk management. The 2023 Verizon Data Breach Investigations Report revealed that 74% of breaches involved the human element, highlighting the importance of employee engagement in risk management.
To foster a risk-aware culture:
- Implement regular security awareness training for all employees
- Encourage open communication about potential risks and near-misses
- Recognize and reward employees who identify and report security issues
Organizations that prioritize security awareness training experience 70% fewer security incidents (according to a study by the Ponemon Institute).
Evaluate and Improve Framework Continuously
The IT risk landscape constantly evolves, necessitating regular review and updates to risk management frameworks. An Accenture study found that 68% of business leaders feel the risks they face are increasing in volume and complexity.
To keep your framework current:
- Conduct annual comprehensive risk assessments
- Test and evaluate the effectiveness of existing controls regularly
- Stay informed about emerging threats and adjust strategies accordingly
Organizations that review and update their risk management frameworks at least annually are 2.5 times more likely to mitigate security incidents effectively (according to research by Deloitte).
Harness Automation and AI
Leveraging automation and artificial intelligence can significantly enhance IT risk management efforts. A McKinsey report suggests that AI-enabled risk management could save up to $1 trillion in the banking industry.
Key areas where automation and AI can improve risk management include:
- Threat detection and response
- Vulnerability scanning and patching
- Compliance monitoring and reporting
Automated patch management systems can reduce the time to patch critical vulnerabilities by up to 60% (as reported in a study by Ponemon Institute).
Financial Planning and Risk Management
Effective IT risk management is closely tied to financial planning and forecasting. By integrating risk management considerations into financial strategies, organizations can better allocate resources for security initiatives and prepare for potential financial impacts of IT incidents.
Final Thoughts
An effective Information Technology Risk Management Framework protects organizations in today’s digital landscape. We explored key steps from risk identification to incident response planning, emphasizing the importance of business alignment and risk-aware culture. Regular evaluation and improvement of your framework will help you stay ahead of potential security incidents.

The future of IT risk management will likely involve artificial intelligence, increased focus on supply chain security, and new approaches to securing remote workforces. These trends will shape how organizations protect their digital assets and maintain a competitive edge.
Pro Hockey Advisors understands the unique challenges professional hockey organizations face in managing IT risks. Our expertise in career management, contract negotiations, and financial planning can help you navigate the complex intersection of sports and technology (while safeguarding your organization’s future in an increasingly digital world).


