Third-party relationships are essential for business growth, but they come with inherent risks. At Pro Hockey Advisors, we understand the importance of managing these risks effectively.
The interagency guidance on third-party relationships: risk management provides a framework for organizations to navigate this complex landscape. In this post, we’ll explore practical strategies to identify, assess, and mitigate third-party risks, helping you safeguard your business and maintain strong partnerships.
Identifying and Assessing Third-Party Risks
Mapping Your Third-Party Landscape
The first step in managing third-party risks is to create a comprehensive inventory of all your third-party relationships. This includes vendors, suppliers, contractors, and even less obvious partners (like cloud service providers or marketing agencies). A 2023 Deloitte survey revealed that 65% of organizations struggle to maintain an accurate third-party inventory, underscoring the importance of this step.
Assessing Relationship Nature
After identifying your third parties, evaluate the nature of each relationship. Consider these factors:
- Data access: What sensitive information can they access?
- Operational impact: How critical are they to your daily operations?
- Regulatory implications: Do they handle tasks subject to specific regulations?
Common Risks to Watch
Third-party relationships introduce various risks. The 2022 Verizon Data Breach Investigations Report found that 62% of System Intrusion incidents stemmed from an organization’s supply chain. Key areas of concern include:
- Data breaches and cybersecurity vulnerabilities
- Operational disruptions
- Compliance violations
- Reputational damage
- Financial instability of the third party
Effective Risk Assessment Techniques
To evaluate these risks effectively, use a mix of qualitative and quantitative assessment techniques:
- Security questionnaires: Send detailed surveys to assess a third party’s security practices.
- On-site audits: For critical partners, conduct in-person evaluations of their facilities and processes.
- Financial health checks: Review financial statements to gauge stability.
- Compliance certifications: Verify relevant industry certifications (e.g., ISO 27001, SOC 2).
Leveraging Technology for Risk Assessment
Modern risk management tools can significantly streamline the assessment process. Platforms like SecurityScorecard or BitSight provide continuous monitoring of third-party security postures. These tools offer real-time insights into potential vulnerabilities, allowing for proactive risk mitigation.

The identification and assessment of third-party risks is an ongoing process that requires regular reassessments as both your business relationships and the risk landscape evolve. This thorough understanding of your third parties and their associated risks forms the foundation for developing a robust third-party risk management strategy, which we will explore in the next section.
Building a Robust Third-Party Risk Strategy
Crafting Your Risk Management Framework
A well-structured risk management framework forms the backbone of your third-party risk strategy. Define your organization’s risk appetite and tolerance levels to prioritize risks that need immediate attention.
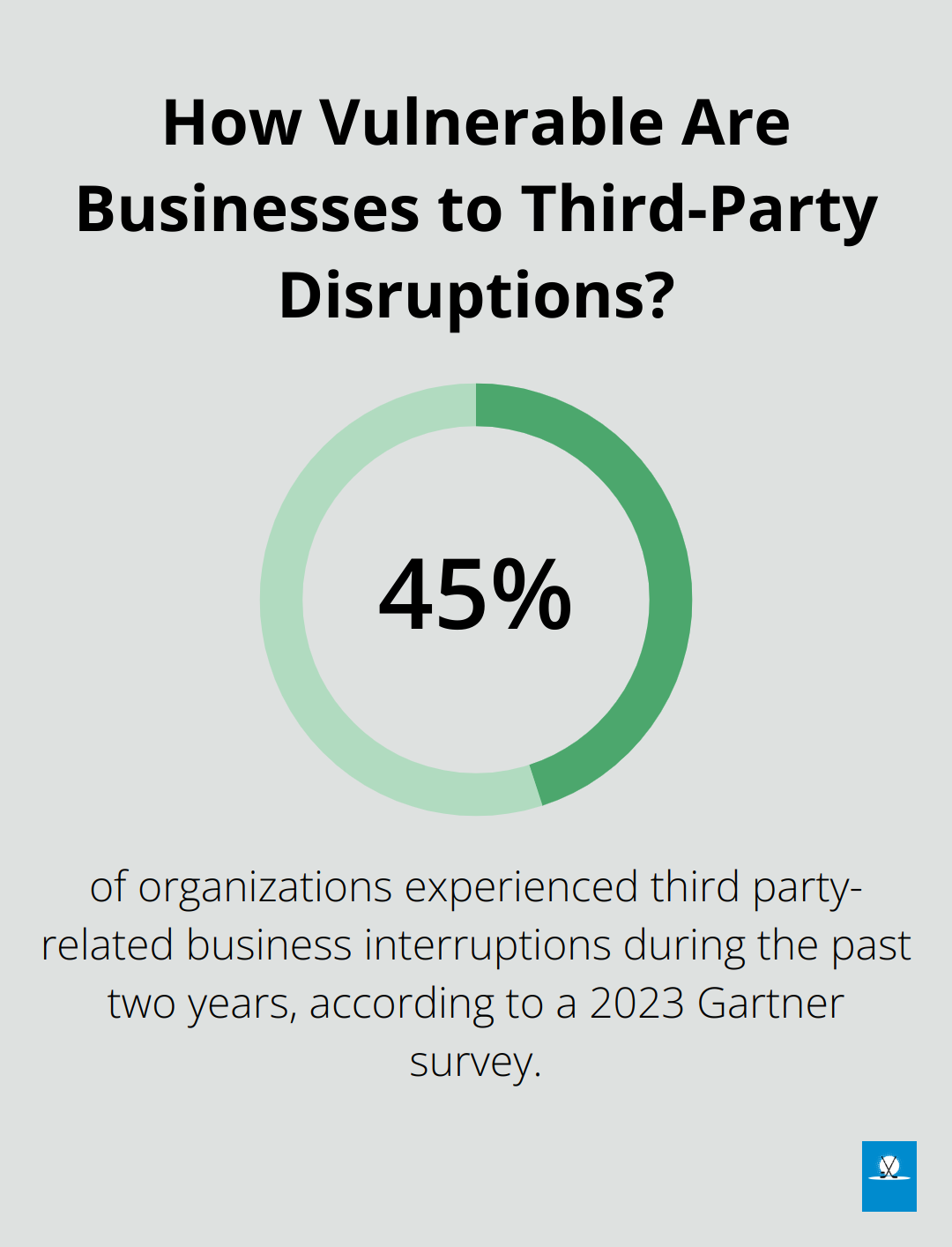
Establish a cross-functional team to oversee third-party risk management. Include representatives from legal, IT, procurement, and relevant business units. A 2023 Gartner survey found that 45% of organizations experienced third party-related business interruptions during the past two years.
Implementing Effective Policies and Procedures
Clear policies and procedures ensure consistent risk management across your organization. Develop guidelines that outline:
- Vendor selection criteria
- Risk assessment methodologies
- Contractual requirements for third parties
- Incident response protocols
- Ongoing monitoring processes
Make these policies easily accessible and update them regularly to reflect changes in the regulatory landscape or your organization’s risk profile.
Streamlining Due Diligence Processes
Thorough due diligence is essential when onboarding new third parties or reassessing existing relationships. Implement a tiered approach based on the criticality and potential risk exposure of each relationship. For high-risk vendors, consider:
- Comprehensive security assessments
- Financial stability checks
- Compliance and regulatory reviews
- On-site audits or virtual assessments
Automate parts of this process to increase efficiency and consistency. Vendor risk management platforms can significantly streamline due diligence efforts.
Measuring Success with Key Performance Indicators
To gauge the effectiveness of your third-party risk management strategy, establish clear performance metrics and KPIs. These might include:
- Time to complete risk assessments
- Percentage of vendors meeting security requirements
- Number of security incidents attributed to third parties
- Cost savings from risk mitigation efforts
Review these metrics regularly to identify areas for improvement and demonstrate the value of your risk management program to stakeholders.
The development of an effective third-party risk management strategy requires continuous adaptation. As we move forward, we’ll explore how to maintain and improve your strategy through ongoing monitoring and mitigation efforts.
How to Stay Ahead of Third-Party Risks
Implement Continuous Monitoring
Continuous monitoring allows organizations to identify and address risks in real-time. Businesses using threat intelligence and advanced analytics are 2.5 times more likely to detect and respond to breaches before significant damage occurs. Use automated tools that provide real-time alerts on changes in your third parties’ risk profiles. These tools can monitor financial health, cybersecurity posture, and regulatory compliance.
Conduct Regular Assessments
While continuous monitoring provides ongoing insights, periodic in-depth assessments offer a comprehensive view of your third-party landscape. Schedule annual or bi-annual reviews of your critical vendors, focusing on:
- Changes in their business operations or ownership
- Updates to their security practices and infrastructure
- Compliance with evolving regulations
- Performance against agreed-upon service level agreements (SLAs)

The frequency and depth of these assessments should align with the risk level associated with each third party.
Take Swift Corrective Action
Quick action is essential when issues arise. Develop a clear escalation process for addressing risks, involving relevant stakeholders from your organization and the third party. This might include:
- Immediate notification of security incidents
- Collaborative problem-solving sessions
- Implementation of additional security controls
- Revision of contractual terms if necessary
The Ponemon Institute is dedicated to independent research and education that advances responsible information use and privacy management practices within businesses.
Leverage Advanced Technologies
Artificial intelligence (AI) and machine learning (ML) revolutionize third-party risk management. These technologies can analyze vast amounts of data to identify patterns and predict potential risks before they materialize. For example, AI-powered tools can:
- Analyze news and social media for reputational risks
- Detect anomalies in third-party behavior that might indicate a security breach
- Automate the assessment of vendor questionnaires and security documentation
While these technologies offer powerful capabilities, it’s important to combine them with human expertise for optimal results.
Foster a Risk-Aware Culture
Create a culture of risk awareness within your organization. Educate employees about the importance of third-party risk management and their role in identifying and reporting potential issues. Encourage open communication and provide clear channels for reporting concerns (e.g., dedicated email addresses or internal reporting systems).
Final Thoughts
Managing third-party relationship risks requires constant vigilance and adaptation. The interagency guidance on third-party relationships: risk management provides a solid foundation for organizations to build upon. AI and machine learning will play an increasingly significant role in predicting and mitigating risks, while regulatory frameworks are expected to evolve.

At Pro Hockey Advisors, we understand the importance of managing risks effectively in business partnerships. Our expertise in career management and contract negotiations can help navigate complex relationships and mitigate potential risks. A proactive approach to third-party risk management protects your organization from potential threats and strengthens your partnerships.
The future of third-party risk management will likely see a greater emphasis on supply chain resilience and cybersecurity. Global events continue to highlight vulnerabilities in these areas. Organizations that stay informed, leverage the right tools, and foster a risk-aware culture will be well-equipped to face the challenges and opportunities that lie ahead in the evolving landscape of third-party relationships.


